How the world's largest democracy casts its ballots
Explaining the equipment and the process by which hundreds of millions of ballots are collected and counted in India.
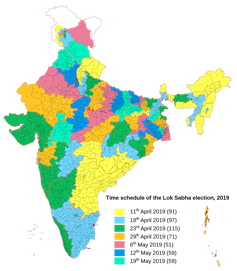
About 600 million Indian citizens are expected to cast their votes over a period of 39 days ending May 19, in the ongoing election for their country’s parliament. There are roughly 900 million eligible voters, and the country has typically seen about two-thirds of them turn out to polling places.
I have been working on the security of electronic voting systems for more than 15 years, and, along with other colleagues, have been interested in understanding how a nation can tally that many votes cast over such a long period. India uses a domestically designed and manufactured electronic voting machine – as many as 4 million of them at 1 million polling places, at least some in extremely remote locations.
The first version of the Indian electronic voting machine debuted in the state election in Kerala in 1982. Now they’re used in elections throughout the country, which happen on different days in different areas.
How does it work?
When a voter arrives at the polling place, she presents a photo ID and the poll officer checks that she is on the electoral roll. When it’s her turn to vote, a polling official uses an electronic voting machine’s control unit to unlock its balloting unit, ready to accept her vote.
The balloting unit has a very simple user interface: a series of buttons with candidate names and symbols. To vote, the voter simply presses the button next to the candidate of her choice.
After each button press, a printer prints out the voter’s choice on paper and displays it to the voter for a few seconds, so the person may verify that the vote was recorded correctly. Then the paper is dropped into a locked storage box.
The whole system runs on a battery, so it does not need to be plugged in.
When it’s time for the polling place to close at the end of the voting day, each electronic voting machine device and paper-record storage box is sealed with wax and tape bearing the signatures of representatives of the various candidates in that election, and stored under armed guard.

After the election period is over and it’s time to tally the votes, the electronic voting machines are brought out, the seals opened and the vote counts for each control unit are read out from its display board. Election workers hand-tally these individual machine totals to obtain the election results for each constituency.
Security protections – and concerns
The Indian electronic voting machine primarily runs on specialized hardware and firmware, unlike the voting machines used in the U.S., which are software-intensive. It is intended for the single purpose of voting and specially designed for that, rather than relying on a standard operating system like Windows, which needs to be regularly updated to patch detected security vulnerabilities.
Each machine requires only a connection between a balloting unit and a control unit; there are no provisions to connect an electronic voting machine to a computer network, much less the internet – including wirelessly.
This design does offer some protections against possible tampering with how votes are recorded and tallied. The Election Commission of India has repeatedly claimed that the electronic voting machines are tamper-proof. However, a scholarly study has demonstrated there are ways to rig the machines. In particular, the simplicity of the design allows for simple attacks, such as intercepting and modifying the signal carried over the machine’s cable.
The Election Commission has not made public any independent security evaluations, so it’s unclear exactly what is – or isn’t – possible. Parties that lose elections often suspect malfeasance and question the equipment.
Manufacturing the machines
As I and others have observed, when the machines are being made, there are a number of opportunities for someone to physically tamper with an electronic voting machine in ways that preelection device testing might not detect. The machines’ software is designed, written and tested at two electronics companies owned by the government of India: Bharat Electronics Limited and Electronics Corporation of India Limited. The chips for the machines are manufactured outside India. In earlier versions of the machine, the chip manufacturer also wrote the machine code into the chip; today the electronics companies do it themselves.
At any time during manufacture, testing and maintenance, it may be possible to introduce counterfeit chips or swap out other components that could let hackers alter the results.
The Election Commission of India argues that any manipulation or error would be detected because the electronic voting machine is tested frequently and candidate representatives have opportunities to participate in mock elections immediately before a machine is used in a real election. However, it is possible to make changes that will not be detected. Testing can reveal only some problems, and the absence of problems during testing does not mean that problems do not exist.
Auditing the machines’ results
There is, however, a mechanism for detecting attacks – that printed-out paper bearing the vote and stored securely with the electronic equipment. A 2013 Supreme Court directive asked the Election Commission to create that process to protect the integrity of the balloting process.

In each constituency, five electronic voting machines will have their results audited by comparing a manual count of the printouts with the electronic tallies. (This means about 1% or 2% of each constituency’s machines will be tested.) Opposition parties have asked the Supreme Court to order audits of half of all electronic voting machines, but that may not happen with this year’s election.
While the electronic voting machine system is useful and functional, officials and observers shouldn’t assume there’s no way to tamper with the results. The Election Commission should certainly continue to improve testing and provide public reports of independent testing. However, because no technology can be tamper-proof, each election outcome should be verified by a manual audit, to ensure that the results are correct, whatever they may be.
Poorvi Vora receives funding from the National Science Foundation and has received funding from the Maryland Procurement Office in the past. She is affiliated with Verified Voting and the Election Verification Network.
Read These Next
Enforcing Prohibition with a massive new federal force of poorly trained agents didn’t go so well in
Both Prohibition and current mass deportation efforts were hastily built, staffed by people permitted…
I’m a philosopher who tries to see the best in others – but I know there are limits
Seeing someone charitably requires a balancing act between taking them seriously and trying to see the…
Last nuclear weapons limits expired – pushing world toward new arms race
The expiration of the New START treaty has the US and Russia poised to increase the number of their…